Featured
Table of Contents
- – [Solved] Before You Begin
- – Vpn Tunnel: What Is It And How Does It Work?
- – Use The Best Vpn Tunneling Protocol
- – What Is A Vpn Tunnel, And How It Works?
- – What Is A Vpn?
- – What Is The Secure Socket Tunneling Protocol...
- – Types Of Vpn Tunneling
- – What Is A Vpn Tunnel?
- – Understanding Vpn Ipsec Tunnel Mode And ...
- – Vpn Protocols - What They Are And The Differ...
[Solved] Before You Begin
This provides more flexibility than producing an SSH tunnel to a single port as formerly described. SOCKS can free the user from the limitations of linking just to a predefined remote port and server. If an application does not support SOCKS, a proxifier can be utilized to redirect the application to the local SOCKS proxy server.
This produces tun (layer 3, default) or tap (layer 2) virtual user interfaces on both ends of the connection. This permits regular network management and routing to be utilized, and when utilized on routers, the traffic for a whole subnetwork can be tunneled.
Vpn Tunnel: What Is It And How Does It Work?
VPNs can work on any gadget that links to the web and can run a VPN app, including your smartphone, computer, and some clever Televisions. All you need to do is download a VPN app to your gadget and follow the guidelines to connect to a VPN server. When you connect to the VPN server, an encrypted connection is negotiated in between your gadget and the VPN server.
In the last 20 years, mass security has been deployed versus whole populations in many countries.
Use The Best Vpn Tunneling Protocol
This leaves your traffic susceptible to interception, including any passwords or other sensitive data you get in. A bigger concern is that the data collected from you by any of the above trackers will suffer a data leakage that exposes your information. A VPN will not resist all (and even most) leaks, however it is one more layer of protection in an information area designed to extract your data.
Lots of streaming sites are not accessible in particular nations. If you're traveling abroad, you can link to a VPN server back home to log in to your account. Proton VPN users can access lots of popular streaming websites by linking to a Plus server because nation. There are other benefits of a VPN that are very important in certain usage cases: Prevent peers from seeing your real IP address when using P2P file sharing (Bit, Torrent).
What Is A Vpn Tunnel, And How It Works?
The protocols are basically a set of directions the computer systems must follow to establish the encrypted connection, keep it, and send your web traffic inside it. VPN procedures have different strengths and weaknesses. Some are quicker or slower, more steady or less steady, or more resistant to attacks. Here's a quick overview: An older VPN protocol with several known vulnerabilities.
Layer two tunneling procedure (L2TP) and Internet Procedure security (IPSec) are two protocols that often interact to negotiate the server connection and handle the file encryption, respectively. This is a more protected system than PPTP, but it may have vulnerabilities and usually isn't as fast or steady as newer protocols.
What Is A Vpn?
A VPN tunnel is simply a metaphor for the encryption a VPN utilizes to hide your information as it travels in between your device and the VPN server. Many internet traffic is noticeable to others on the network, so 3rd parties, like your web service company or government firms, can see what websites you check out and where you lie.
VPN tunneling likewise avoids hackers from misusing data by securing them from end to end. The majority of VPNs utilize AES-256 file encryption, which militaries, banks, and federal governments use to protect confidential information. It is technically impossible to break the AES-256 encryption without a cipher secret, as it would take trillions of years to do so.
What Is The Secure Socket Tunneling Protocol (Sstp)?
Like IKe, V2, Open, VPN offers powerful speed and security for VPN tunneling. Wire, Guard is the latest and most safe VPN encryption procedure.
Proxies only work for web browsers and not apps. If you utilize an app despite linking to the proxy, your real IP address will still be exposed.
Types Of Vpn Tunneling

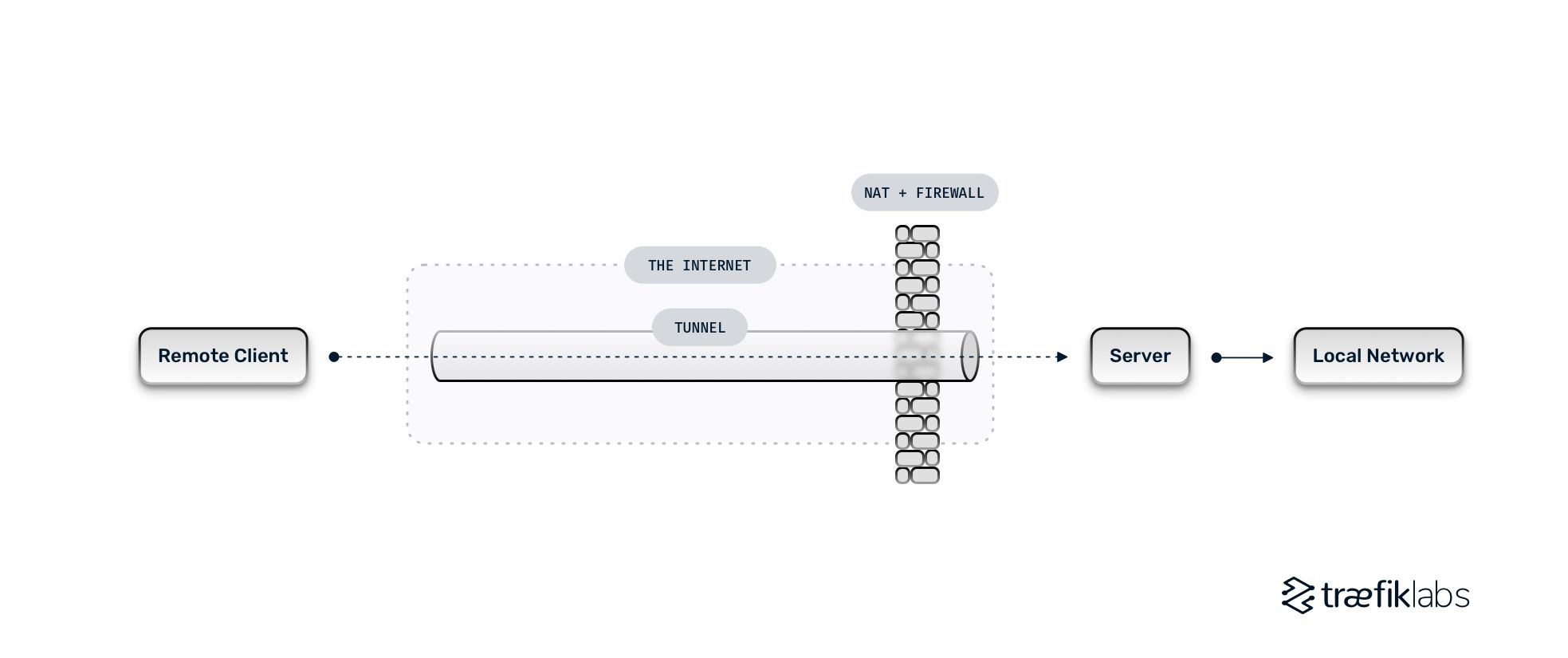
VPN technology is simple, however there are. All of this can get really technical, so here's a quick rundown of which types of VPN and tunneling procedures are right for your business. Both remote gain access to and site-to-site VPN options resolve the very same problems using various techniques. The end goal is still securing business resources from unapproved access.
Organizations mainly use this type to. You can think of it as a VPN connection making a safe and secure pathway from your device to access sensitive documents or company materials on the other end.
What Is A Vpn Tunnel?
The majority of companies embrace generally hosted somewhere else, using huge information. Setting remote gain access to VPN up might not be the most practical option as in those cases, the information would be going from users' device to the central center, to the information center and back. So not only this might introduce.
It's worth keeping in mind that you need to prepare depending on the number of users accessing them. It requires separately setting up for both networks, and it works best for cases when you have numerous remote websites.
Understanding Vpn Ipsec Tunnel Mode And ...
It supplies detailed guidelines on product packaging the data and what checks to perform when it reaches its location. It is twofold file encryption the encrypted message sits in the data packet, which is further encrypted once again.
There even are proprietary Wire, Guard implementations like Nord, Lynx. A VPN protocol should be the last thing off the list that you need to be choosing. First,: remote gain access to or site-to-site. It should narrow down your list of alternatives. It's worth noting that neither remote access nor site-to-site are the only possibilities to set up an Internet-based VPN.
Vpn Protocols - What They Are And The Differences ...

I.e., if you're currently utilizing routers that natively support Open, VPN, it might make more sense to use them rather than throwing them out to get ones that can deal with Wireguard.
What is a VPN Tunnel & How VPN Tunneling Functions? Information, Prot is supported by its audience. When you buy through links on our website, we might earn a commission. This, however, does not affect the evaluations in our reviews. Find out More. As we browse the web, we leave crumbs of browsing data on the pages we check out.
Table of Contents
- – [Solved] Before You Begin
- – Vpn Tunnel: What Is It And How Does It Work?
- – Use The Best Vpn Tunneling Protocol
- – What Is A Vpn Tunnel, And How It Works?
- – What Is A Vpn?
- – What Is The Secure Socket Tunneling Protocol...
- – Types Of Vpn Tunneling
- – What Is A Vpn Tunnel?
- – Understanding Vpn Ipsec Tunnel Mode And ...
- – Vpn Protocols - What They Are And The Differ...
Latest Posts
Vpn.group: We Know Vpn - Reviews And Information -
5 Best Business Vpns In 2023 - Most Secure And Reliable
10 Best Vpn Services For Startups 2023 - Truic
More
Latest Posts
Vpn.group: We Know Vpn - Reviews And Information -
5 Best Business Vpns In 2023 - Most Secure And Reliable
10 Best Vpn Services For Startups 2023 - Truic